Contactless, secure-less?
We use contactless technology on a daily basis to pay groceries, ride public transport, access buildings, enter parkings or hotel rooms.
Have you ever thought about how it worked, or how secure it is?
Card’s anatomy
Let’s put a contactless card behind a flashlight to get more insight on what’s inside the plastic.

What comes into view is a microchip attached to an antenna coil, but there is no apparent power source for the microchip.
These cards are called passive tags—they need a reader to operate. Examples of such readers include (but are not limited to) payment terminals, electronic door locks, or even smartphones!
To work, the reader produces an electromagnetic field. Whenever the passive tag is moved close enough to the reader—usually up to 10 cm—a current is induced in the antenna coil, and the microchip receives power.
This principle is known as electromagnetic induction. The same mechanism is used for wireless charging or levitating light bulbs for example.
RFID and NFC in a nutshell
The generic technology behind these contactless cards is called Radio Frequency IDentification (aka RFID). It relies on radio waves in order to identify items at various distances using different frequencies (from 30 kHz to 3 GHz).
Since it has been patented in 1983, RFID enabled many use cases across different industries: retail, transportation, animal identification, sports, etc. However, due to its large spectrum, vendor implementations were sometimes lacking consistency. Contactless cards were commonly operating at various frequencies (usually 125 kHz or 13.56 MHz), using proprietary communication and security protocols.
In order to drive a wider adoption, improve interoperability and security, market leaders Philips and Sony teamed-up in 2002 to establish the Near Field Communication standard (aka NFC). The standard is based on their respective experience with MIFARE and FeliCa RFID smart card systems.
NFC operates solely at 13.56 MHz and supports 3 modes: reader/writer, card emulation, and peer-to-peer.
The NFC Forum non-profit organization has been in charge of the NFC standard since 2004 and many companies (such as Apple, Google, Visa, or Mastercard) have joined forces with Sony and NXP (formerly part of Phillips).
House of cards
Even though NFC is a well-defined set of standards, it has been created based on existing RFID smart cards systems. The standard took them into consideration and that led to supporting different types of tags in the NFC specification.
In truth, there exist many tags which are more or less compliant with the NFC specifications.
As most smartphones are NFC-capable nowadays, they can be used to get more info on our contactless cards. I would recommend the excellent NFC Tools app for that, available on both Android and iPhone.
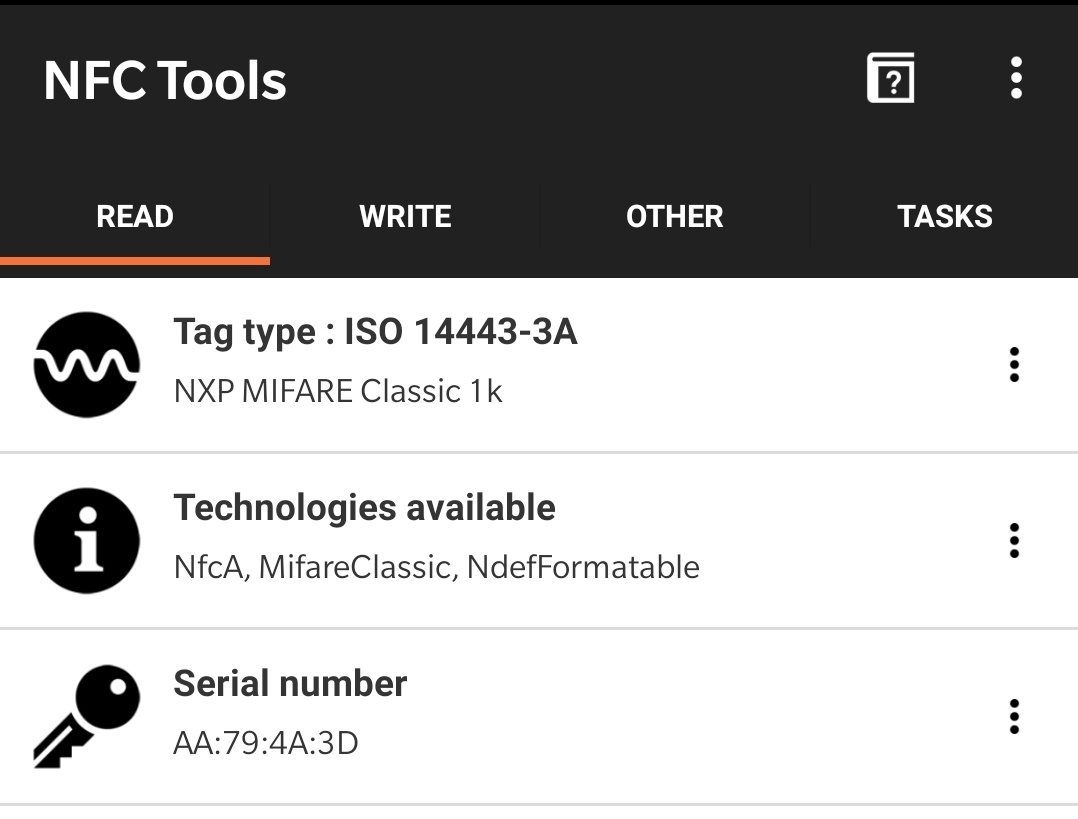
My gym card
Once you’ve opened the app, approach an NFC tag to the back of your phone and move it slowly around until it is detected. Information about the card should pop up.
In my case, all my contactless cards are a variant of the MIFARE product:
- MIFARE Classic 1k: gym card, office access card, and home access key fob (main entrance)
- MIFARE DESFire: public transport card
- MIFARE Plus: VISA and Mastercard
MIFARE Classic
The MIFARE Classic 1k card is quite old (introduced in 1994) and suffers from multiple security vulnerabilities. However it is still one of the most popular smart card as of today. Some countries even use it in their national ID card (eg. Emirates ID in UAE).
The Mifare Classic Tool app lets us interact with this type of card by reading and writing it.
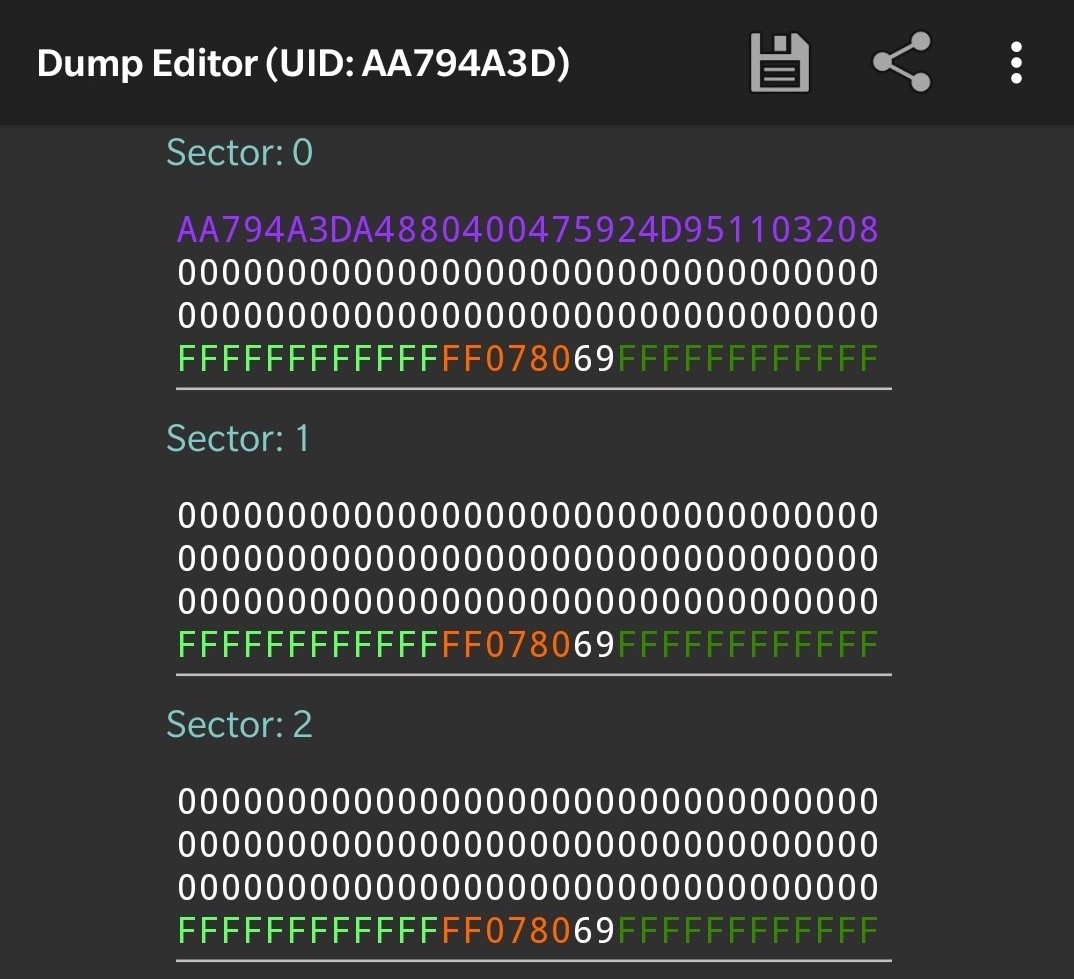
Data on my gym card
The card contains 1kB of storage, divided in 16 sectors.
A sector is a standalone storage unit and consists of 4 blocks (on the screenshot above each line represents a block encoded in hexadecimal).
On a given sector, the first 3 blocks can be used to store arbitrary data. All read/write operations must be authenticated with a secret key, according to authentication rules specified in the last block.
The only exception to this is the very first block of the card. It is known as the manufacturer block (in purple on the screenshot). It mainly contains the card ID (in my case AA794A3D), the rest of the data is not too relevant. This block is written at the factory when the card is built and is immutable. It also does not require authentication: it is world-readable.
What’s wrong with my gym card?
My gym card is essentially a blank card, all blocks are empty and secret keys have been kept to their default value FFFFFFFFFFFF.
The gym maintains a database with its members and associated card IDs. Whenever someone comes to the gym and approaches their access card to the reader, it will open the door if it can match the card ID with a valid membership.
This scenario is very vulnerable to identity theft. These cards are constantly ready to spit out their ID, it would only take a second for an attacker to sniff it with nothing other than a smartphone!
Once the ID is known, the card can easily be cloned to another counterfeit “UID writable” card or emulated with a phone.
The aforementioned vulnerability is attributable to a naive implementation rather than the MIFARE Classic 1k per se, the card ID was originally designed as an anti-collision mechanism (i.e, when multiple cards are present in the reader electromagnetic field). At no point was it supposed to be used as an authentication mechanism.
Security by obscurity
Many implementations do use secret keys to store data. Eg. the account balance on a vending machine card, room number and reservation dates on a hotel card, etc.
In these scenarios the MIFARE Classic cards rely on a proprietary encryption algorithm called CRYPTO1.
This in-house algorithm was reversed-engineered in 2007 and researchers published papers describing multiple attacks.
All in all, any MIFARE Classic card could be cracked in less than 10 seconds.
In response, new hardened cards have been released by NXP, they’ve also been cracked in 2015. Since then, NXP publicly acknowledged that their algorithm is insecure and encouraged users to move to newer products for security relevant applications.
Upgrading The Hard Way
The most disturbing part isn’t that CRYPTO-1 was cracked—algorithms do get broken eventually, only to be replaced by new ones.
However, the lack of an easy upgrade path is one of the reasons why the MIFARE Classic card is still widely used even 15 years after it has been cracked.
When you’ve issued millions of cards like The Netherlands did with their public transport card OV-chipkaart, moving away to more secure smart cards is a costly organizational challenge that can take years, and it did.
With no regulatory authority, some organizations might even deliberately choose not to upgrade after weighing the pros and cons (cost of upgrading vs cost of fraud, reputational risk, etc.).
Smart cards are quite rigid, they’re specifically tailored for a given cryptographic algorithm and it cannot change. On the other hand, we have a much more powerful and generic-purpose piece of hardware at the constant reach of our fingertips…
The cardless way
The card emulation mode is similar to the reader/writer mode, except that the smart card is swapped for an NFC device, such as a smartphone.
This is how Google Pay or Apple Pay work for example, customers can simply tap their smartphone instead of their credit card.
Historically, card emulation was only possible through a secure element, a chip which is either embedded in the phone or the SIM card. The secure element is isolated from the rest of the phone and acts as a vault to securely store sensitive data. However it can only be used with a few selected apps that are chosen by the manufacturer.
Nowadays more apps are able to emulate cards. On Android for example, it can be done through the host-based card emulation feature (aka Android HCE).
To some extent, Android HCE addresses some vulnerabilities of traditional systems. We’ve seen for instance that many facilities were relying on the card ID for access control purposes. This is explicitly prevented by Android HCE:
“HCE devices should be assumed to have a random UID. This means that on every tap, the UID that is presented to the reader will be a randomly generated UID. Because of this, NFC readers should not depend on the UID of HCE devices as a form of authentication or identification.”
Card emulation also comes with its own set of challenges. As Android HCE doesn’t use a secure element, developers must make sure that card data is safely stored and can’t be tampered with.
Fortunately, Android provides many security features for the applications it runs, such as sandboxing capabilities. Should any vulnerability be discovered, security updates could quickly be pushed to users.
Smart-hands?
Vulnerabilities can also arise on the reader side or during data transmission. This is what happened with the recently unveiled VISA relay attack, which can affect both smart cards or emulated cards interchangeably.
As we’ve seen, smart cards are mostly vulnerable to social engineering. Even though they are quite secure in theory, smartphones seem to provide a wider attack surface due to their inherent complexity.
Card emulation is very convenient and usually preferred by users. Many organizations are going into this direction as part of their digital transformation journey. It is increasingly common to see mobile apps being provided in lieu of public transport or loyalty cards.
This trend might even have been accelerated by the COVID-19 pandemic, as we become more concerned about physical distancing.
Wallets are definitely an endangered species that will be replaced eventually. Smartphones look to be their natural successor but biometrics are just around the corner. Amazon is currently experimenting with their new contactless technology based on the palm of our hands…


